Shalom Kravim Seebernetiyim! (Greetings cyber warriors)
We are back to conclude our series in Reconnaissance Like a Cyber Scout. In this part, the author will show a solution to a problem that intelligent people may get perceive. And what would this problem be? We have shown more than 60 tools with different goals throughout the articles and as we said earlier, we need to be smart in the way we treat our data.
The automation of the tools, which will be executed to result in an output with unique findings is like an athlete’s zone, the Olympus of the gods… and that is exactly what we will show through the ReconFTW tool.
Automation with ReconFTW & Web GUI Contribution
ReconFTW
This tool automates the entire process of reconnaissance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses a lot of techniques (passive, brute-force, permutations, certificate transparency, source code scraping, analytics, DNS records…) for subdomain enumeration which helps you get the maximum and the most interesting subdomains so that you can be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, port scanning, screenshots, and nuclei scanning on your target.
So, what are you waiting for? Go! Go! Go! 👹👹👹

In addition, ReconFTW has the possibility of integration with more than 60 API services, being the tool with the greatest refinement in output information. We recommend taking a look at the wiki.
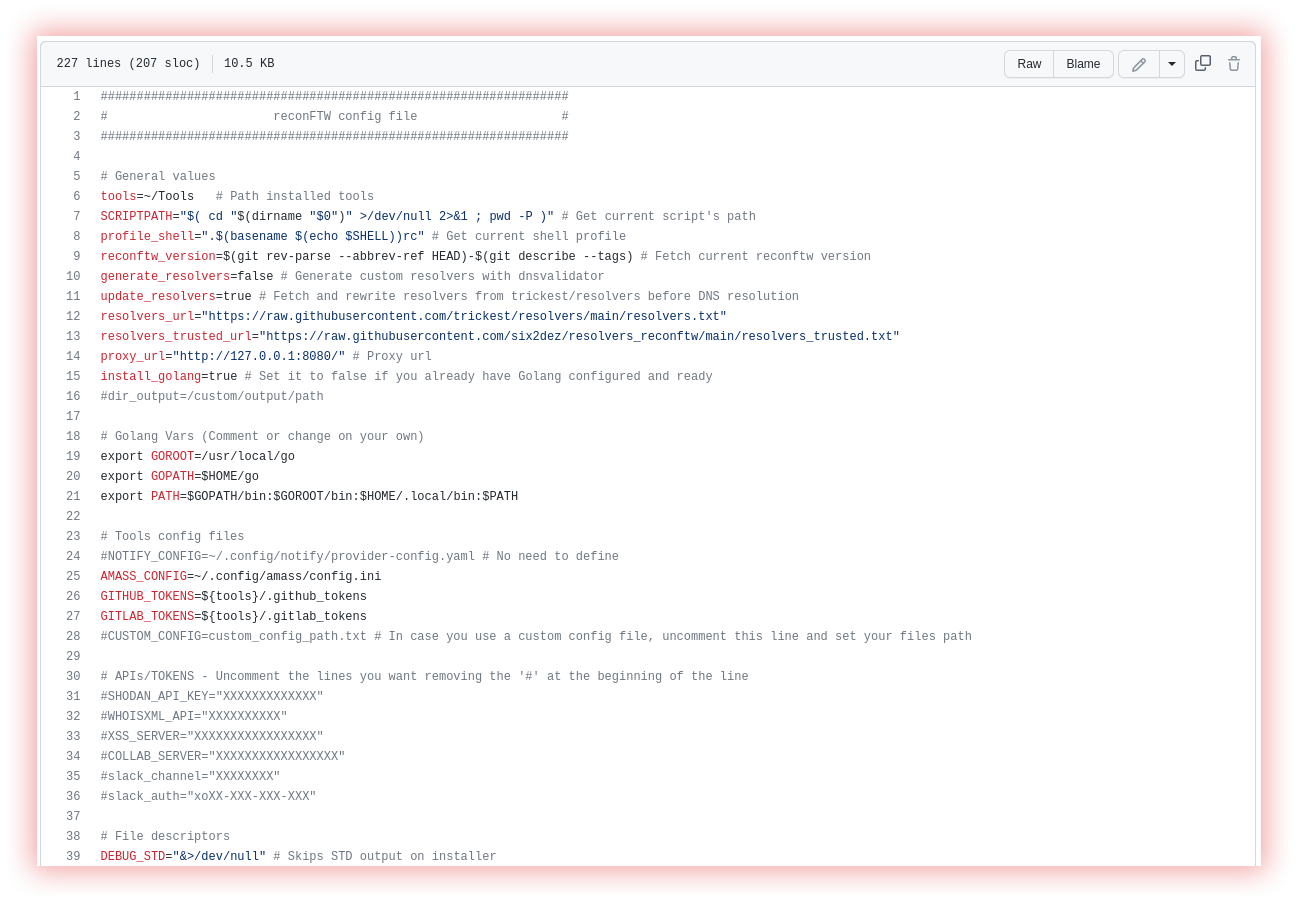
Execution flow of ReconFTW:
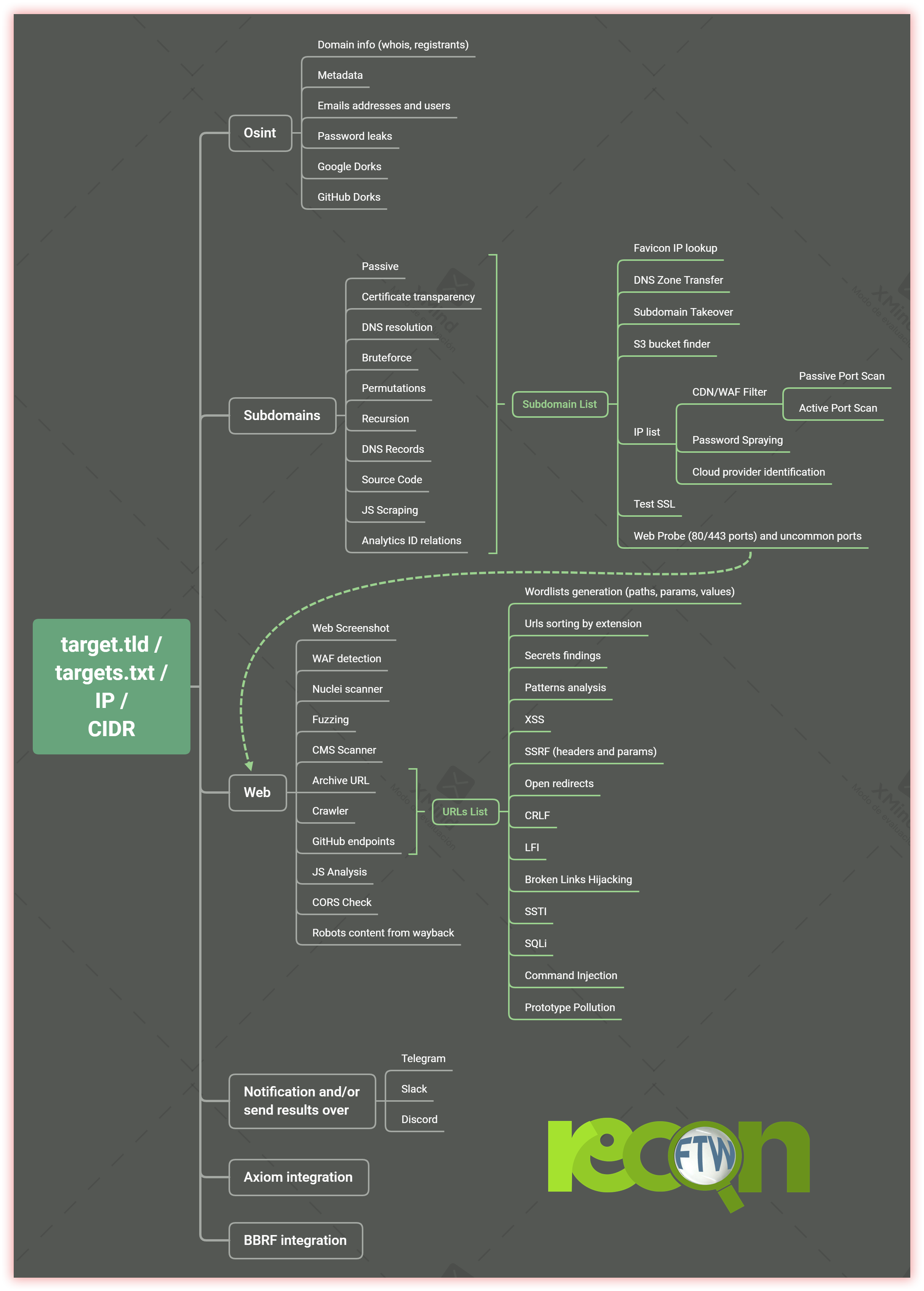
Output generated by ReconFTW:
After using the tool for a long time, I always encountered the problem of generating many output files and this made it difficult to organize all the information because they are separated into different folders and text files.
With the mindset of an open-source contributor, I contacted Six2dez, the creator of the ReconFTW tool, to ask if I could work on a contribution. This would be a modular, responsive, web interface. Six2dez promptly and in an extremely extraordinary way accepted me to participate and contribute to the ReconFTW project.
Below we will show the entire contribution process with our ideas and things on the to-do list.
Modular Web Interface Contribution:
The MobSF tool has always been a reference for me with the idea of an interface that handles a lot of information. For mobile lovers, you’ve probably already used it a few times in your tests. MobSF was built in Django and has a clean and direct style for the data, without many graphics and “excesses” that for us, technicians, are not very important.

After literally months, thousands of code lines, and hair that fell out in the process, we got an application in Django with the same idea as MobSF. One of the differentials is the authentication panel that allows the sharing of scans without providing access to VPS or .ZIP files, the configuration of APIs centrally on one page and others feature that will be added.
Below we have a demo video:
We still have many features/bugs to work on and conclude, we mention the “API CONFIG” page as an example. We also believe that the code can be optimized and the beauty of having a modular application (just a folder called “web” that has all the codes that will handle the bash script “reconftw.sh”), is that it makes implementing new features a bit easier.
We conclude our series on reconnaissance, where we have shown the basics of the theme following with the solution of one “problem” which is the fact that there are many tools, and if we run all of them, it would take a long time to analyze and integrate with other tools. This solution came through ReconFTW, in which we concluded with the exhibition of the contribution that take one year by the main contributor and maintainer of the tool Lucas “luriel” Carmo.
I would like to take this opportunity to thank and give the credit to all people that are involved in this process. Thanks so much, Daniel “d3v” Chactoura who created and correlated all the data structure through file scraping and Django models. To Daniel “daniboy” Lima for creating the authentication and schedule scan page with celery. To Matheus “mx61tt” Tucunduva for having implemented the “New Scan” feature. All the people who motivated/supported me and especially six2dez who is an incredible person that I don’t have words to describe just so much positive energy and wisdom.
With that, I make a call to all hackers around the world who want to help us build something amazing, please help us, and let’s contribute!

